In this blog post, I'll provide some cursory coverage on Ousaban and its initial stage via a Microsoft Installer (MSI) file.
Ousaban is a Latin American banking trojan that's been affecting users for the last few years, primarily across Brazil. According to research from ESET, the way the malware works is the MSI will reach out and download the actual Ousaban payload, which will then be side-loaded into a legitimate application to conduct its credential stealing.
Below I have an image of what the MSI shows in PeStudio, showing a plethora of exports:

I passed the file over to REMnux and did a generic strings check to see if any of the C2 domains were hardcoded in the file. Nothing stood out as conclusive at this point.

Dynamic analysis followed with detonation of the sample, which resulted in the following dialog boxes. I infer that the error message occurred due to either VM detection or an inability to establish communications with its C2 server.


Wireshark and FakeDNS both showed this domain. We didn't see this in the initial analysis, which leads me to believe that it was dynamically generated at runtime:

Researching the domain on VirusTotal, we see that it has several malicious hits and also that it was generated only 6 days prior to this research taking place. The sample was submitted to MalwareBazaar 2 days after the domain was registered.

I briefly want to highlight a tool and a peer in the community who's research brought my attention to it. Tony Lambert recently posted about msitools, a suite of tools available to analyze specimens just like the one I've touched on in this blog post. After my initial research, I decided to download the package and give it a go.

I ran msiinfo on the specimen, which gives the analyst information on the contents of the installer package:
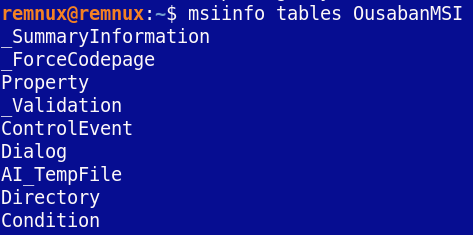
I look for the CustomAction table which, per Tony's phenomenal blog post, is where a lot of malware developers will hide their malicious code when working with MSI's. Sure enough, I ran msidump to dump the file and then analyzed the CustomAction table...


...and we see what looks like obfuscated code! I copy this text and plug it into CyberChef and select "From Charcode" as my recipe:

There we can not only see the URL I identified during my dynamic analysis, but also the file the installer would attempt to download (AW24RT4T56Y76U788I80909.zip). Additionally, further down we see some indication that it may try to write to the "Saved Games" directory as well as references to WMIC with calls to launch a program:

To conclude this cursory analysis, I leave you with this humorous reference in the code to "JimmyNeltronFPS", which lines up with the file being written to "Saved Games." Granted, this is only a function name in the code but regardless, great:

IOCs
Domains:
wschyoilnet[.]com
File hash: 0ed6d539365305787d1625bf6462c93dbd02af768970b6d05f8ca5c6ff2e1b3d
File name downloaded from domain: AW24RT4T56Y76U788I80909.zip
References
Comments